移动应用使用临时凭证直传
更新时间 2023-12-07 21:31:05
最近更新时间: 2023-12-07 21:31:05
本文主要讲解移动应用使用临时凭证直传文件的最佳实践。
实践背景
在移动互联网时代,从手机里的照片到各类文件,移动端APP需要上传到服务器的文件越来越多。开发者可以使用媒体存储来保存这些文件,媒体存储提供的SDK接口可以支持直接在移动端进行文件上传。
访问媒体存储需要使用密钥(AK/SK),但是如果在移动端直接使用长期密钥访问对象存储,遭受黑客攻击就可能会暴露长期密钥,导致对象存储中的文件泄露或被篡改,存在很大的风险。
媒体存储提供STS角色管理功能,可以为移动端颁发一个自定义时效和权限的访问凭证,无需在移动端暴露长期密钥。使用STS授权访问时,请务必按照业务情况,以最细粒度的权限原则进行授权,避免放大临时用户的权限,保证资源访问安全。
应用流程
使用临时凭证直传时,具体应用流程如下:
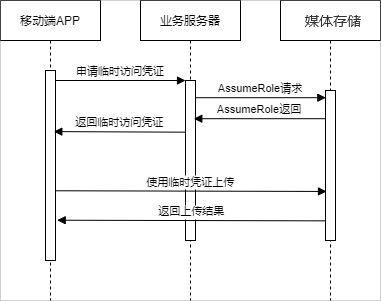
实践步骤
创建用于获取STS访问凭证的角色
通过媒体存储控制台,创建STS角色,并获取对应的arn信息,具体可参考 STS角色管理 。
对应角色授权并且获取STS临时密钥
具体可参照如下java示例:
// STS endPoint
String endPoint = "<sts-endpoint>";
// 在对象存储控制台访问密钥AccessKey和SecretKey。
String accessKey = "<access-key>";
String secretKey = "<secret-key>";
// 填写步骤一获取的角色ARN。
String roleArn = "<role-arn>";
// 设置临时访问凭证的名称.
String roleSessionName = "<session-name>";
// 设置 Policy 允许上传对象
String policy = "{\"Version\":\"2012-10-17\"," + "\"Statement\":[" + "{\"Effect\":\"Allow\","
+ "\"Action\":[\"s3:PutObject\"],"
+ "\"Resource\":[\"arn:aws:s3:::<bucket-name>/*\"]}" + "]}";
// 创建STS Client
BasicAWSCredentials basicAWSCredentials = new BasicAWSCredentials(accessKey, secretKey);
AwsClientBuilder.EndpointConfiguration endpointConfiguration = new AwsClientBuilder.EndpointConfiguration(endPoint, "");
AWSSecurityTokenService stsClient = AWSSecurityTokenServiceClientBuilder.standard()
.withCredentials(new AWSStaticCredentialsProvider(basicAWSCredentials))
.withEndpointConfiguration(endpointConfiguration)
.build();
AssumeRoleRequest assumeRoleRequest = new AssumeRoleRequest();
assumeRoleRequest.setRoleArn(roleArn);
assumeRoleRequest.setRoleSessionName(roleSessionName);
assumeRoleRequest.setPolicy(policy);
AssumeRoleResult assumeRoleRes = stsClient.assumeRole(assumeRoleRequest);
Credentials stsCredentials = assumeRoleRes.getCredentials();
System.out.println("Expiration: " + stsCredentials.getExpiration());
System.out.println("Access Key Id: " + stsCredentials.getAccessKeyId());
System.out.println("Access Key Secret: " + stsCredentials.getSecretAccessKey());
System.out.println("Security Token: " + stsCredentials.getSessionToken());
通过临时密钥访问对象存储资源
本文以Android与IOS应用为例。
- Android
public class MyCredentialsProvider implements AWSCredentialsProvider {
private AWSCredentials credentials;
public MyCredentialsProvider(String ak, String sk, String token) {
this.credentials = new BasicSessionCredentials(ak, sk, token);
}
public synchronized AWSCredentials getCredentials() {
return credentials;
}
public synchronized void refresh() {
}
// 更新ak,sk,token
public synchronized void updateCred(String ak, String sk, String token) {
this.credentials = new BasicSessionCredentials(ak, sk, token);
}
}
String accessKey = "<your-access-key>";
String secretKey = "<your-secret-access-key>";
String endPoint = "<your-endpoint>";
String sessionToken = "<your-session-token>";
MyCredentialsProvider credProvider = new MyCredentialsProvider(accessKey, secretKey, sessionToken);
ClientConfiguration clientConfig = new ClientConfiguration();
clientConfig.setProtocol(Protocol.HTTP);
AmazonS3Client mS3Client = new AmazonS3Client(credProvider, clientConfig);
mS3Client.setEndpoint(endPoint);
- IOS
#define ACCESS_KEY @"<your-access-key>"
#define SECRET_KEY @"<your-secret-key>"
#define ENDPOINT @"<your-endpoint>"
#define SESSION_TOKEN @"<your-session-token>"
-(id)initWithToken {
if (self = [super init]) {
AWSBasicSessionCredentialsProvider *credentialsProvider = [[AWSBasicSessionCredentialsProvider alloc] initWithAccessKey:ACCESS_KEY secretKey:SECRET_KEY sessionToken:SESSION_TOKEN];
AWSEndpoint *endPoint = [[AWSEndpoint alloc] initWithURLString:ENDPOINT];
AWSServiceConfiguration *configuration = [[AWSServiceConfiguration alloc]
initWithRegion:AWSRegionUSEast1
endpoint:endPoint
credentialsProvider:credentialsProvider];
[AWSServiceManager defaultServiceManager].defaultServiceConfiguration = configuration;
self.s3 = [AWSS3 defaultS3];
}
return self;
}
