介绍
WireGuard 是一款开源的下一代 VPN 协议。它由 Jason Donenfeld 等人用 C 语言编写,代码库仅约 4000 行。具有诸多优点:采用 Curve25519、ChaCha20 和 Poly1305 等先进加密技术保障安全;基于 UDP 传输,性能高、延迟低;配置简单,易于理解和部署;还支持 Linux、Windows、macOS、iOS 和 Android 等多平台。可应用于个人隐私保护、远程办公、站点互联、跨云连接等场景。
**相比ipsec,**配置相对简单,代码简洁,配置文件通常只需几个关键参数,易于理解和部署, 且在一些测试中,转发速率比 IPsec 高出 15%-23%,时延降低 20% 左右。。
本文将介绍wireguard的安装方式、直接模式、中继模式的环境搭建过程,通过过装包的方式演示其通信过程。
状态机
- Idle(空闲): 在这个状态下,WireGuard 接口尚未激活或配置。没有数据包被处理。
- Listening(监听): 当接口被激活后,WireGuard 开始监听来自对端的握手请求。在此状态下,它准备接收第一个数据包并进行密钥交换。
- Handshake(握手): 在此状态下,WireGuard 进行密钥交换过程。这涉及到双方互换公钥,并建立临时会话密钥。
- Established(已建立): 握手成功之后,隧道进入正常操作模式,在这种状态下,可以加密/解密数据包,并通过隧道传输。
- Retransmission(重传): 如果需要重新发送握手消息或数据包确认,则进入此状态。
- Expiration(过期): 会话密钥具有有效期限。一旦过期,需要重新进行握手以生成新的会话密钥。
install
目前对于debian系统,可以通过 apt 的方式直接安装 wiregurad
# env
# uname -a
Linux ctyun 5.10.0-26-amd64 #1 SMP Debian 5.10.197-1 (2023-09-29) x86_64 GNU/Linux
sudo apt install openresolv
sudo apt-get install wireguard
拓扑结构

环境搭建预计debian系统,通过创建 namespace的方式模拟不同的机器。其中client1 、client2 和server建立wiregurad隧道。
中继模式: client1 <-> client2 互访
直连模式: client1 <-> server 或者 client2 <-> server
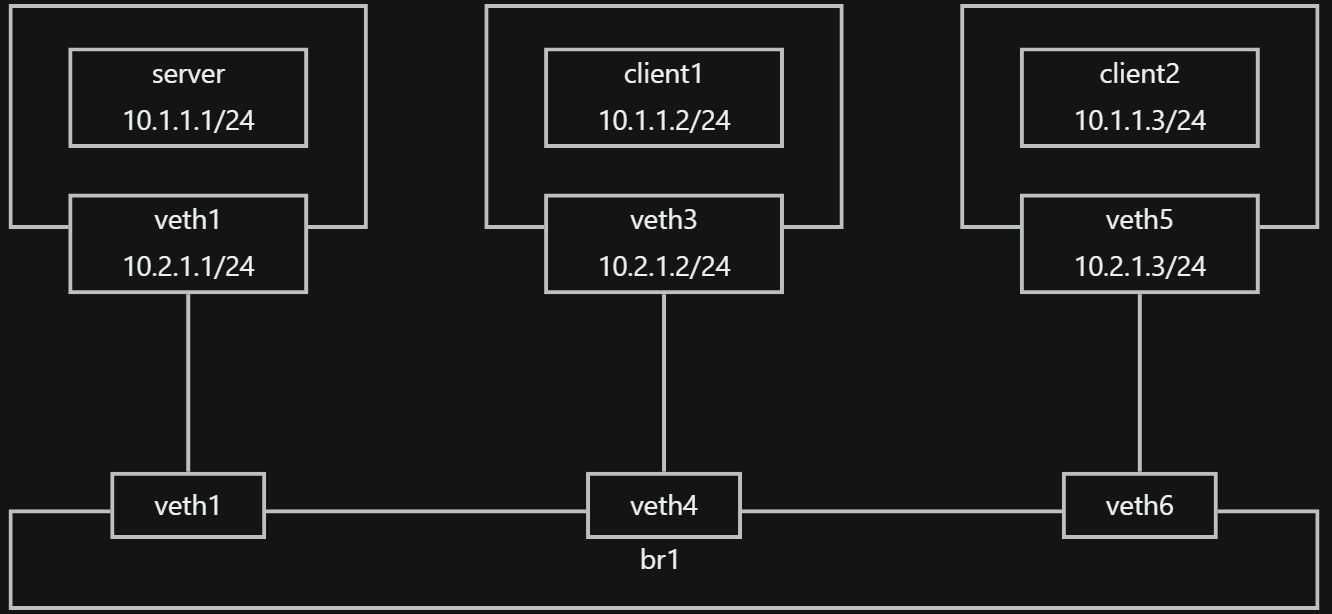 创建拓扑的shell 命令如下:
创建拓扑的shell 命令如下:
# create ns
ip netns add server
ip netns add client1
ip netns add client2
# create veth
ip link add veth1 type veth peer name veth2
ip link add veth3 type veth peer name veth4
ip link add veth5 type veth peer name veth6
ip link set veth1 netns server
ip link set veth3 netns client1
ip link set veth5 netns client2
ip link add br1 type bridge
ip link set veth2 master br1
ip link set veth4 master br1
ip link set veth6 master br1
# port up
ip link set br1 up
ip link set veth2 up
ip link set veth4 up
ip link set veth6 up
ip netns exec server ip link set veth1 up
ip netns exec client1 ip link set veth3 up
ip netns exec client2 ip link set veth5 up
# ip
ip netns exec server ip a a 10.2.1.1/24 dev veth1
ip netns exec client1 ip a a 10.2.1.2/24 dev veth3
ip netns exec client2 ip a a 10.2.1.3/24 dev veth5
config
在启动wiregurad之前需要创建其工作目录、密钥、配置文件等准备工作。
工作目录
配置wiregurad的工作目录
cd /etc/wireguard
key 生成
生成 server、client1、client2 的公钥、密钥文件
# server
wg genkey | tee server_privatekey | wg pubkey > server_publickey
# client1
wg genkey | tee client1_privatekey | wg pubkey > client1_publickey
# client2
wg genkey | tee client2_privatekey | wg pubkey > client2_publickey
server
生成server端的配置文件
echo "
[Interface]
PrivateKey = $(cat server_privatekey) # 填写本机的privatekey 内容
Address = 10.1.1.1/24
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -A FORWARD -o wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -D FORWARD -o wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
ListenPort = 50814 # 注意该端口是UDP端口
DNS = 8.8.8.8
MTU = 1420
[Peer]
PublicKey = $(cat client1_publickey) # 填写对端的publickey 内容
AllowedIPs = 10.1.1.2/32
[Peer]
PublicKey = $(cat client2_publickey) # 填写对端的publickey 内容
AllowedIPs = 10.1.1.3/32 " > server.conf
client1
生成client1 的配置文件
echo "
[Interface]
PrivateKey = $(cat client1_privatekey) # 填写本机的privatekey 内容
Address = 10.1.1.2/24
DNS = 8.8.8.8
MTU = 1420
[Peer]
PublicKey = $(cat server_publickey) # 填写对端的publickey 内容
Endpoint = 10.2.1.1:50814
AllowedIPs = 0.0.0.0/0, ::0/0
PersistentKeepalive = 25 " > client1.conf
client2
生成client2 的配置文件
echo "
[Interface]
PrivateKey = $(cat client2_privatekey) # 填写本机的privatekey 内容
Address = 10.1.1.3/24
DNS = 8.8.8.8
MTU = 1420
[Peer]
PublicKey = $(cat server_publickey) # 填写对端的publickey 内容
Endpoint = 10.2.1.1:50814
AllowedIPs = 0.0.0.0/0, ::0/0
PersistentKeepalive = 25 " > client2.conf
start
准备好密钥和配置文件后,就可以通过 wg-quick 命令直接启动各个端点
ip netns exec server wg-quick up server
ip netns exec client1 wg-quick up client1
ip netns exec client2 wg-quick up client2
stop
当需要关闭wg 服务器, 可以通过如下方式进行。
ip netns exec server wg-quick down server
ip netns exec client1 wg-quick down client1
ip netns exec client2 wg-quick down client2
check
当服务启动后可以通过查看 wg 的运行状态,及通过抓包的方式,了解wg的运行状态及数据包通信流程。
status
当wg服务启动后, 可以通过wg 命令查看目前隧道的状态。 当启动后没有故障,server ,client1, client2 的状态如下所示。
# server
ip netns exec server wg
interface: server
public key: CB1jYlC8eKcbtQPyWMIAgA5vpO9zLcVV/LxqbPtoNAw=
private key: (hidden)
listening port: 50814
peer: 6vVRIPVLIvpkhKlVHTSTECPKYbVjVH4J9eJ/B2GIJD0=
endpoint: 10.2.1.3:56295
allowed ips: 10.1.1.3/32
latest handshake: 22 seconds ago
transfer: 180 B received, 92 B sent
peer: TzPKQC1vAd5rQCsXBT0/DVnn6w+f/bJ0aBmY7lo3yws=
endpoint: 10.2.1.2:45409
allowed ips: 10.1.1.2/32
latest handshake: 22 seconds ago
transfer: 180 B received, 92 B sent
# client1
ip netns exec client1 wg
interface: client1
public key: TzPKQC1vAd5rQCsXBT0/DVnn6w+f/bJ0aBmY7lo3yws=
private key: (hidden)
listening port: 45409
fwmark: 0xca6c
peer: CB1jYlC8eKcbtQPyWMIAgA5vpO9zLcVV/LxqbPtoNAw=
endpoint: 10.2.1.1:50814
allowed ips: 0.0.0.0/0, ::/0
latest handshake: 1 minute, 6 seconds ago
transfer: 92 B received, 244 B sent
persistent keepalive: every 25 seconds
# client2
ip netns exec client2 wg
interface: client2
public key: 6vVRIPVLIvpkhKlVHTSTECPKYbVjVH4J9eJ/B2GIJD0=
private key: (hidden)
listening port: 56295
fwmark: 0xca6c
peer: CB1jYlC8eKcbtQPyWMIAgA5vpO9zLcVV/LxqbPtoNAw=
endpoint: 10.2.1.1:50814
allowed ips: 0.0.0.0/0, ::/0
latest handshake: 1 minute, 23 seconds ago
transfer: 92 B received, 276 B sent
persistent keepalive: every 25 seconds
tcpdump
可以通过装包的方式了解中级模式和直连模式的数据包的转发流程。具体信息如下。
直连模式
直连模式可以通过 client1 <-> client2 通信,进行了解;
# 连模式
ip netns exec client1 ping 10.1.1.1
# 数据包通信流程
# 报文转发路径
wg 加密封装 wg 解封装解密
client1 -> veth3 -> veth1 -> server
中继模式
中继模式的数据转发路径如下
# 中继模式
ip netns exec client1 ping 10.1.1.3
# 报文转发路径
wg 加密封装 wg 解封装解密 wg 加密封装 wg 解封装解密
client1 -> veth3 -> veth1 -> server -> veth1 -> veth5 - > client2
通过在各个节点进行抓包,了解中继模式的通信流程
# cleint1
ip netns exec client1 tcpdump -nnn -vvv -e -i client1
tcpdump: listening on client1, link-type RAW (Raw IP), snapshot length 262144 bytes
^C06:13:41.494921 ip: (tos 0x0, ttl 64, id 26117, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 71, length 64
06:13:41.495938 ip: (tos 0x0, ttl 63, id 24733, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 71, length 64
06:13:42.496415 ip: (tos 0x0, ttl 64, id 26303, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 72, length 64
06:13:42.497935 ip: (tos 0x0, ttl 63, id 24788, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 72, length 64
06:13:43.498361 ip: (tos 0x0, ttl 64, id 26474, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 73, length 64
06:13:43.498968 ip: (tos 0x0, ttl 63, id 24864, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 73, length 64
# veth3
ip netns exec client1 tcpdump -nnn -vvv -e -i veth3
tcpdump: listening on veth3, link-type EN10MB (Ethernet), snapshot length 262144 bytes
^C06:14:23.895150 96:38:80:a8:bd:6d > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170:(tos 0x0, ttl 64, id 35444, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.2.45409 > 10.2.1.1.50814: [bad udp cksum 0x16a0 -> 0x25e1!] UDP, length 128
06:14:23.895522 92:3d:50:f9:dd:01 > 96:38:80:a8:bd:6d, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 27443, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.2.45409: [bad udp cksum 0x16a0 -> 0xbb5b!] UDP, length 128
06:14:24.896477 96:38:80:a8:bd:6d > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 35608, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.2.45409 > 10.2.1.1.50814: [bad udp cksum 0x16a0 -> 0xfe1e!] UDP, length 128
06:14:24.897075 92:3d:50:f9:dd:01 > 96:38:80:a8:bd:6d, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 27543, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.2.45409: [bad udp cksum 0x16a0 -> 0x8a87!] UDP, length 128
# veth1
ip netns exec server tcpdump -nnn -vvv -e -i veth1
tcpdump: listening on veth1, link-type EN10MB (Ethernet), snapshot length 262144 bytes
^C06:15:45.809597 96:38:80:a8:bd:6d > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170:(tos 0x0, ttl 64, id 45421, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.2.45409 > 10.2.1.1.50814: [bad udp cksum 0x16a0 -> 0x4622!] UDP, length 128
06:15:45.809881 92:3d:50:f9:dd:01 > 4a:67:32:32:04:42, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 208, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.3.56295: [bad udp cksum 0x16a1 -> 0x87a7!] UDP, length 128
06:15:45.810184 4a:67:32:32:04:42 > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 42514, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.3.56295 > 10.2.1.1.50814: [bad udp cksum 0x16a1 -> 0x3e12!] UDP, length 128
06:15:45.810371 92:3d:50:f9:dd:01 > 96:38:80:a8:bd:6d, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 38393, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.2.45409: [bad udp cksum 0x16a0 -> 0x3f80!] UDP, length 128
06:15:46.811049 96:38:80:a8:bd:6d > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 45591, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.2.45409 > 10.2.1.1.50814: [bad udp cksum 0x16a0 -> 0xa9ac!] UDP, length 128
06:15:46.811308 92:3d:50:f9:dd:01 > 4a:67:32:32:04:42, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 343, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.3.56295: [bad udp cksum 0x16a1 -> 0x63c2!] UDP, length 128
06:15:46.811613 4a:67:32:32:04:42 > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 42724, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.3.56295 > 10.2.1.1.50814: [bad udp cksum 0x16a1 -> 0x14f8!] UDP, length 128
06:15:46.811849 92:3d:50:f9:dd:01 > 96:38:80:a8:bd:6d, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 38579, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.2.45409: [bad udp cksum 0x16a0 -> 0x08f7!] UDP, length 128
# server
ip netns exec server tcpdump -nnn -vvv -e -i server
tcpdump: listening on server, link-type RAW (Raw IP), snapshot length 262144 bytes
^C06:16:20.068355 ip: (tos 0x0, ttl 64, id 45514, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 228, length 64
06:16:20.068377 ip: (tos 0x0, ttl 63, id 45514, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 228, length 64
06:16:20.068833 ip: (tos 0x0, ttl 64, id 44190, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 228, length 64
06:16:20.068843 ip: (tos 0x0, ttl 63, id 44190, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 228, length 64
06:16:21.069866 ip: (tos 0x0, ttl 64, id 45607, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 229, length 64
06:16:21.069887 ip: (tos 0x0, ttl 63, id 45607, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 229, length 64
06:16:21.070299 ip: (tos 0x0, ttl 64, id 44325, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 229, length 64
06:16:21.070309 ip: (tos 0x0, ttl 63, id 44325, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 229, length 64
06:16:22.071244 ip: (tos 0x0, ttl 64, id 45608, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 230, length 64
06:16:22.071255 ip: (tos 0x0, ttl 63, id 45608, offset 0, flags [DF], proto ICMP (1), length 84)
# veth5
ip netns exec client2 tcpdump -nnn -vvv -e -i veth5
tcpdump: listening on veth5, link-type EN10MB (Ethernet), snapshot length 262144 bytes
^C06:17:03.478154 92:3d:50:f9:dd:01 > 4a:67:32:32:04:42, ethertype IPv4 (0x0800), length 170:(tos 0x0, ttl 64, id 11337, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.3.56295: [bad udp cksum 0x16a1 -> 0xfc09!] UDP, length 128
06:17:03.478441 4a:67:32:32:04:42 > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 52891, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.3.56295 > 10.2.1.1.50814: [bad udp cksum 0x16a1 -> 0x497a!] UDP, length 128
06:17:04.478774 92:3d:50:f9:dd:01 > 4a:67:32:32:04:42, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 11377, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.1.50814 > 10.2.1.3.56295: [bad udp cksum 0x16a1 -> 0xf8b2!] UDP, length 128
06:17:04.478992 4a:67:32:32:04:42 > 92:3d:50:f9:dd:01, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 64, id 53112, offset 0, flags [none], proto UDP (17), length 156)
10.2.1.3.56295 > 10.2.1.1.50814: [bad udp cksum 0x16a1 -> 0x7c7a!] UDP, length 128
# client2
ip netns exec client2 tcpdump -nnn -vvv -e -i client2
tcpdump: listening on client2, link-type RAW (Raw IP), snapshot length 262144 bytes
^C06:17:25.572310 ip: (tos 0x0, ttl 63, id 52957, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 293, length 64
06:17:25.572331 ip: (tos 0x0, ttl 64, id 51944, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 293, length 64
06:17:26.573637 ip: (tos 0x0, ttl 63, id 53161, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.1.2 > 10.1.1.3: ICMP echo request, id 24682, seq 294, length 64
06:17:26.573661 ip: (tos 0x0, ttl 64, id 52028, offset 0, flags [none], proto ICMP (1), length 84)
10.1.1.3 > 10.1.1.2: ICMP echo reply, id 24682, seq 294, length 64