准备
示例信息如下:
- 操作系统:CentOS 6.9
- Master节点:cdh01.hadoop
- Slave节点:cdh02.hadoop
- 客户端节点:cdh03.hadoop
- Realm:HADOOP.CHINATELECOM.CN
- 数据库管理员对应的principal:admin/admin
开启或关闭以下服务:
# 关闭防护墙
$ sudo service iptables stop
# 关闭SElinux
$ sudo sudo setenforce 0
# 开启时钟同步
$ sudo nptd start安装Kerberos服务端和客户端
# 服务端
$ sudo yum install krb5-server krb5-libs krb5-auth-dialog -y
# 客户端
$ sudo yum install krb5-workstation krb5-libs krb5-auth-dialog -y配置Master KDC
以下都是在Master节点上操作
配置文件
- krb5.conf
- 默认路径:
/etc/krb5.conf - 环境变量:KRB5_CONFIG
- 默认路径:
- kdc.conf
- 默认路径:
/var/kerberos/krb5kdc/kdc.conf - 环境变量:KRB5_KDC_PROFILE
- 默认路径:
- kadm5.acl
- 默认路径:
/var/kerberos/krb5kdc/kadm5.acl
- 默认路径:
示例配置
krb5.conf
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = HADOOP.CHINATELECOM.CN
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
renewable = true
[realms]
HADOOP.CHINATELECOM.CN = {
kdc = cdh01.hadoop
kdc = cdh02.hadoop
admin_server = cdh01.hadoop
}kdc.conf
[kdcdefaults]
kdc_ports = 88,750
[realms]
HADOOP.CHINATELECOM.CN = {
kadmind_port = 749
acl_file = /var/kerberos/krb5kdc/kadm5.acl
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
key_stash_file = /var/kerberos/krb5kdc/.k5.HADOOP.CHINATELECOM.CN
max_renewable_life = 7d 0h 0m 0s
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
default_principal_flags = +preauth
}kadm5.acl
*/admin@HADOOP.CHINATELECOM.CN *创建principal数据库
先把上面的配置好,再创建数据库
$ sudo kdb5_util create -r HADOOP.CHINATELECOM.CN -s
# 需要输入两次密码
Initializing database '/usr/local/var/krb5kdc/principal' for realm 'HADOOP.CHINATELECOM.CN',
master key name 'K/M@HADOOP.CHINATELECOM.CN'
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key: <= Type the master password.
Re-enter KDC database master key to verify: <= Type it again.-r:指定Realm,如果不指定,则使用default_realm的值- 一个Realm对应一个数据库,多个Realm需要创建多个数据库
- 数据库创建成功后,会在
/var/kerberos/krb5kdc目录下生成以下文件:- Kerberos数据库文件:
principal和principal.ok,principal就是默认的数据库名 - 管理数据库文件:
principal.kadm5 - 管理数据库锁文件:
principal.kadmin5.lock - stash file:
.k5.HADOOP.CHINATELECOM.CN(用于KDC自身认证,参考:http://web.mit.edu/kerberos/krb5-latest/doc/basic/stash_file_def.html)
- Kerberos数据库文件:
- 初始化后数据库中包含的principals
$ sudo kadmin.local
Authenticating as principal root/admin@HADOOP.CHINATELECOM.CN with password.
kadmin.local: listprincs
K/M@HADOOP.CHINATELECOM.CN
kadmin/admin@HADOOP.CHINATELECOM.CN
kadmin/cdh01.hadoop@HADOOP.CHINATELECOM.CN
kadmin/changepw@HADOOP.CHINATELECOM.CN
krbtgt/HADOOP.CHINATELECOM.CN@HADOOP.CHINATELECOM.CN
kadmin.local: 启动Kerberos daemons
# 启动KDC服务
$ sudo servicekrb5kdc start
# 启动admin server
$ sudo service kadmin start
# 开机启动
$ sudo chkconfig krb5kdc on
$ sudo chkconfig kadmin on验证服务是否成功启动
查看日志
# 查看kdc日志
$ sudo vim /var/log/krb5kdc.log
# 查看kadmin日志
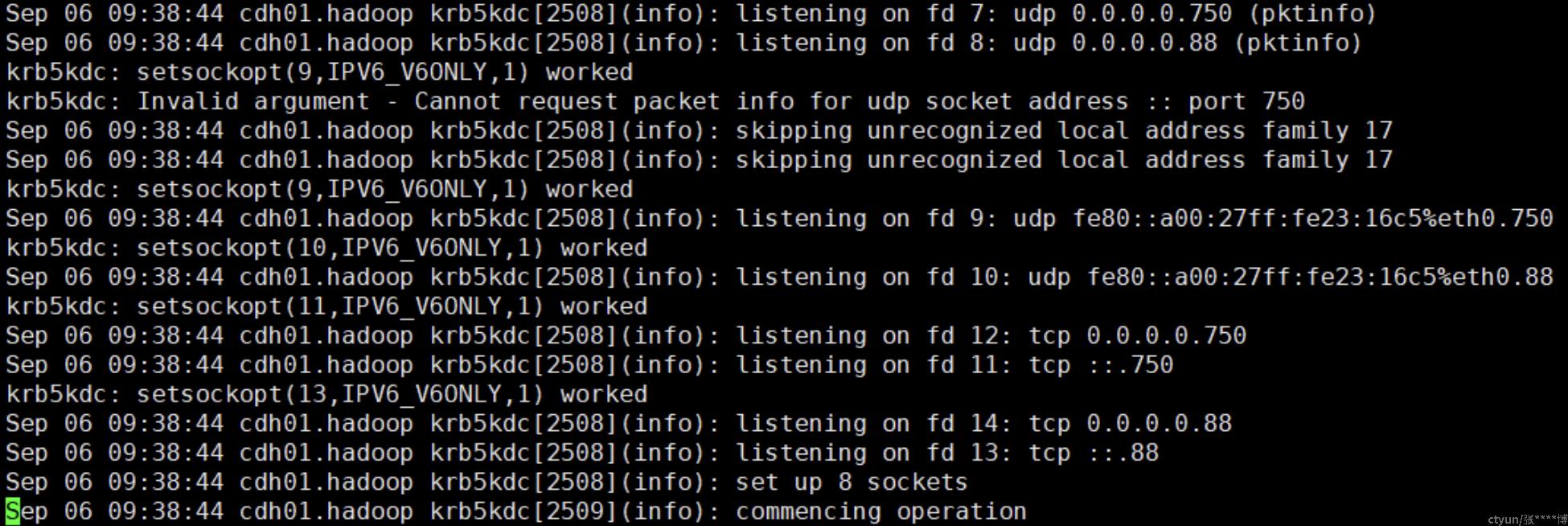
$ sudo vim /var/log/kadmin.logkdc日志内容如下,可以看到监听了两个端口:88(kerberos-iv)和750(kerberos)
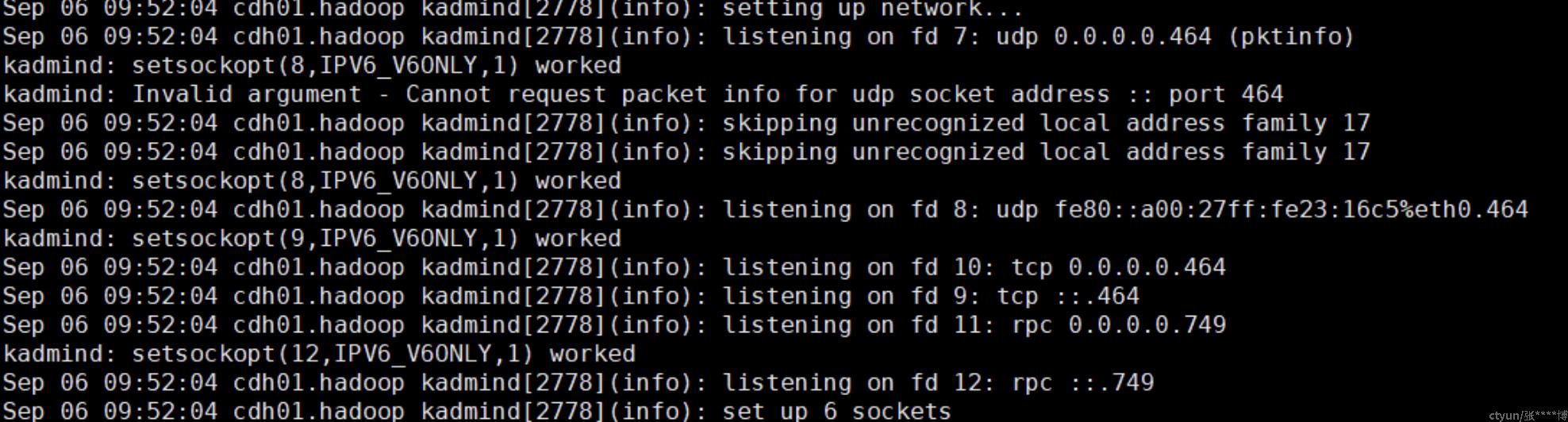
kadmin日志内容,可以看到监听了两个端口:464(kpasswd)和749(kerberos-adm)
通过principal认证来验证
创建一个管理员账号
# 账号:admin/admin,用于kadmin,输入两次密码
addprinc admin/admin
# 生成keytab
xst -norandkey admin/admin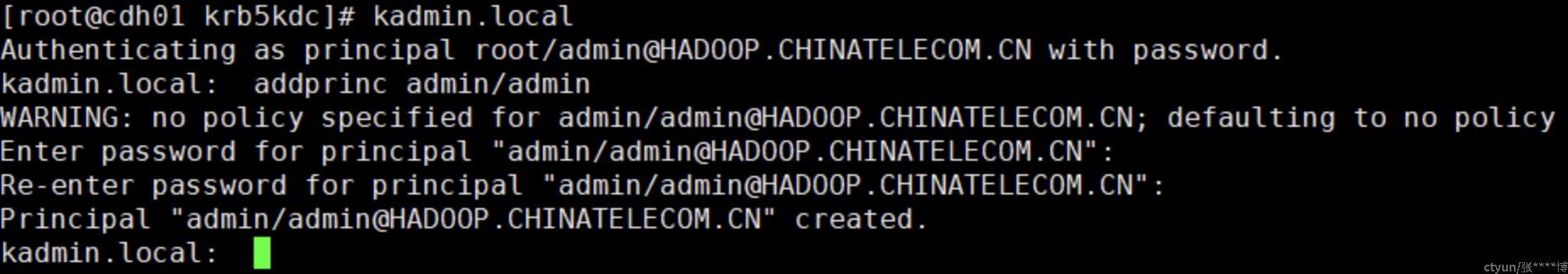
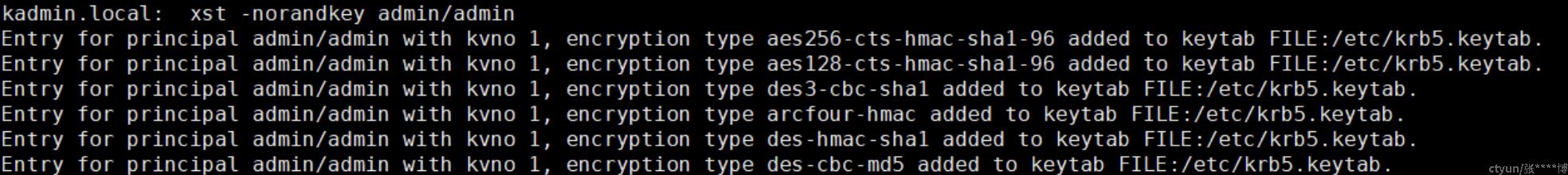
- KVNO是key的版本号
- encryption type表示不同的加密类型
kinit验证
# 获取TGT
kinit -kt /etc/krb5.keytab admin/admin
# 显示当前principal
klist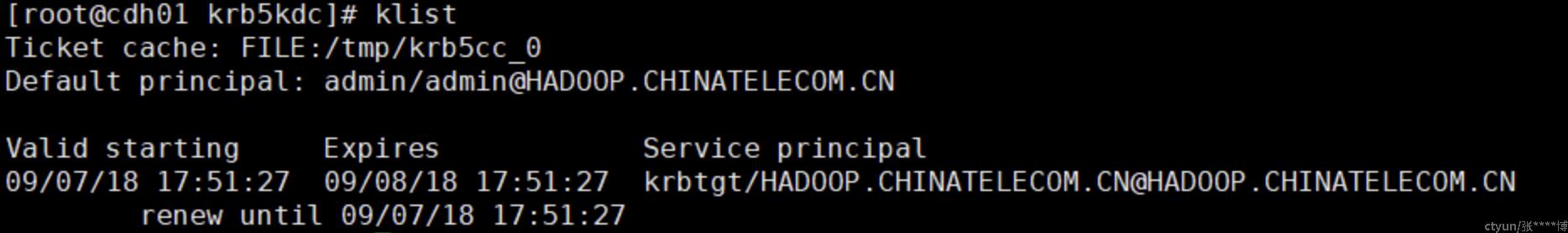
访问kadmin
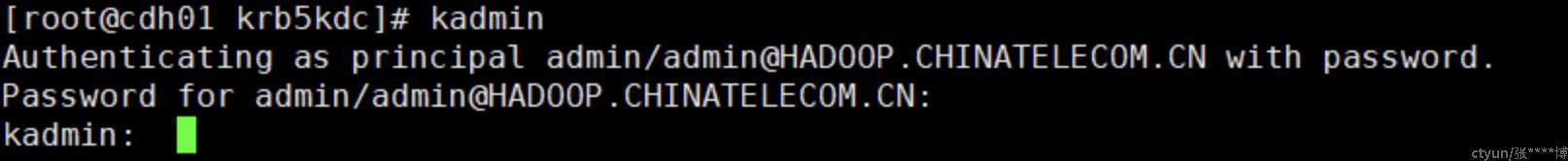
配置Slave KDCs
创建host principals,并生成keytab
$ sudo kamdin.local
# 创建host principals
kadmin.local: addprinc -randkey host/cdh01.hadoop
kadmin.local: addprinc -randkey host/cdh02.hadoop
# 生成keytab,保存到默认的keytab中(/etc/krb5.keytab)
kadmin.local: xst -norandkey host/cdh02.hadoop
kadmin.local: xst -norandkey host/cdh01.hadoop【注】
以上还是要在kadmin.local上运行,kadmin上运行xst不支持-norandkey参数,会导致生成keytab时,密码被随机改变
kadmin: xst -norandkey zhangzb
kadmin: Principal -norandkey does not exist可以看到-norandkey被认为是principal,而不是命令参数
配置文件
将Master上的以下配置文件scp到Slave上对应的目录中
- krb5.conf
- krb5.keytab
- kdc.conf
- kadm5.acl
- stash file(示例中是.k5.HADOOP.CHINATELECOM.CN)
kpropd.acl
在Slaves上创建文件kpropd.acl,添加host principals,kpropd.acl只需放在Slaves上
$ sudo vim /var/kerberos/krb5kdc/kpropd.acl
# 附加以下内容
host/cdh01.hadoop@HADOOP.CHINATELECOM.CN
host/cdh02.hadoop@HADOOP.CHINATELECOM.CN在Slaves上启动kpropd
$ sudo service kprop start将数据库备份到每个Slave上
$ sudo kdb5_util dump /var/kerberos/krb5kdc/slave_datatrans
$ sudo kprop -f /var/kerberos/krb5kdc/slave_datatrans cdh02.hadoop数据库备份
定时备份
配置crontab定期运行以下脚本
#!/bin/sh
kdclist = "cdh02.hadoop"
kdb5_util dump /usr/local/var/krb5kdc/slave_datatrans
for kdc in $kdclist
do
kprop -f /usr/local/var/krb5kdc/slave_datatrans $kdc
done增量备份
创建 kiprop principals
addprinc -randkey kiprop/cdh01.hadoop
addprinc -randkey kiprop/cdh02.hadoop
xst -norandkey kiprop/cdh01.hadoop
xst -norandkey kiprop/cdh02.hadoop修改配置文件
Master和Slaves上的配置都要修改
在kadm5.acl中添加:
kiprop/cdh01.hadoop p
kiprop/cdh02.hadoop p在kdc.conf中realm中添加:
iprop_enable = true
iprop_port = 2121示例中整个kdc.conf配置如下
[kdcdefaults]
kdc_ports = 88,750
[realms]
HADOOP.CHINATELECOM.CN = {
kadmind_port = 749
acl_file = /var/kerberos/krb5kdc/kadm5.acl
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
key_stash_file = /var/kerberos/krb5kdc/.k5.HADOOP.CHINATELECOM.CN
max_renewable_life = 7d 0h 0m 0s
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
default_principal_flags = +preauth
iprop_enable = true
iprop_port = 2121
}重启服务
# Master重启krb5kdc和kamdin服务
$ sudo service krb5kdc restart
$ sudo service kadmin restart
# Slaves重启krb5kdc和kpropd服务
$ sudo service kprop restart
$ sudo service krb5kdc restart启用增量备份后,kadmin就不可用了
CentOS 设置进程数和自启动
vim /etc/sysconfig/krb5kdc
# 设置进程数
KRB5KDC_ARGS="-w 16"
systemctl start krb5kdc
systemctl enable krb5kdc参考资料
https://web.mit.edu/kerberos/krb5-latest/doc/admin/install_kdc.html