前言概述
漏洞或脆弱性(英语:Vulnerability),是指电脑系统安全方面的缺陷,使得系统或其应用数据的保密性、完整性、可用性、访问控制等面临威胁。在《GB/T 25069-2010 信息安全技术 术语》,将脆弱性定义为“资产中能被威胁所利用的弱点”。漏洞利用是攻击成功的常见手段,所以漏洞管理也成为了IT的必备安全能力。关于漏洞的知识点很多,本文主要介绍出自MITRE的一个漏洞评估结构性协议框架-OVAL。这套协议旨在标准化计算机系统安全状态评估, 提供开放和公开的系统安全评估检测内容,他可以用来描述漏洞、软件、补丁、合规。
协议结构
OVAL是一种XML语言结构,提供了一种机器可读的对系统进行安全评估的操作指南。参考下图了解到
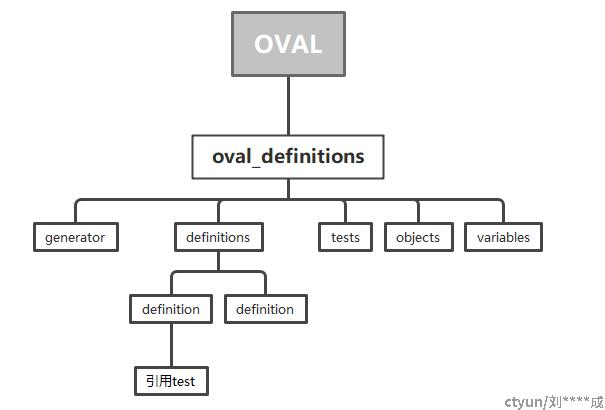
oval_definitions下主要有5元素:
(1)generator,描述文档发布者,版本信息,时间信息等
(2)definitions,描述文档评估的对象,文档的核心元素,主要有以下
(2.1)漏洞(Vulnerability):描述如何根据系统状态判定系统中是否存在某个特定漏洞
(2.2)补丁(Patch):与漏洞定义类似,但它更关注如何判定系统中是否安装了某个特定补丁
(2.3)软件(Inve4ntory):描述如何对系统中是否安装了某个特定的软件进行判定
(2.4)合规(Compliance):描述如何对系统是否满足某个特定的配置要求进行判定。
它会引用一个或多个“测试”,根据“测试”的结果综合判定整体的结果
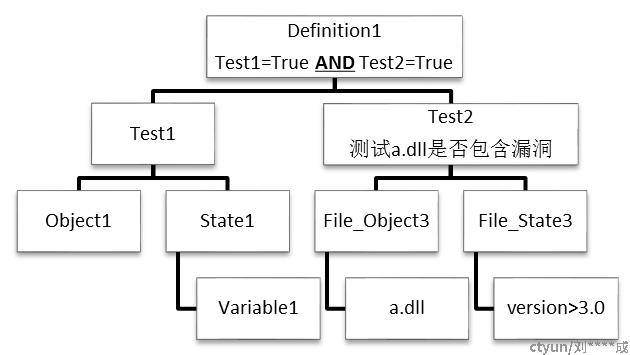
图片来源github:g0dA
(3)tests,描述一组OVAL对象(Object)和状态(State)执行,被definition引用
(4)objects,来描述测试的主题,测试主题类别很多(注册表,组策略,文件,软件包),因此
Object类型也很多,且每种类型结构不同
(5)variables,描述了执行测试时State所需的值,其有三种类型:常量(constant_variable)、本地变量(local_variable)和外部变量(external_variable)。常量定义一个不能在运行时改变的值,本地变量定义在OVAL中直接使用的值,而外部变量通常用于将XCCDF的Value值传递到OVAL中
示例实践
不少软件企业都发布有自己oval库,比如redhat,ubuntu,debian,由于用centos较多,选择redhat的rhel-7-including-unpatched.oval.xml为样例实践认识(篇幅原因,部分xml内容会做省略精简)。
<?xml version="1.0" encoding="utf-8"?>
<oval_definitions xmlns="http://oval.mitre.org/XMLSchema/oval-definitions-5" xmlns:oval="http://oval.mitre.org/XMLSchema/oval-common-5" xmlns:unix-def="http://oval.mitre.org/XMLSchema/oval-definitions-5#unix" xmlns:red-def="http://oval.mitre.org/XMLSchema/oval-definitions-5#linux" xmlns:ind-def="http://oval.mitre.org/XMLSchema/oval-definitions-5#independent" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://oval.mitre.org/XMLSchema/oval-common-5 oval-common-schema.xsd http://oval.mitre.org/XMLSchema/oval-definitions-5 oval-definitions-schema.xsd http://oval.mitre.org/XMLSchema/oval-definitions-5#unix unix-definitions-schema.xsd http://oval.mitre.org/XMLSchema/oval-definitions-5#linux linux-definitions-schema.xsd">
<generator>
<oval:product_name>Red Hat OVAL Patch Definition Merger</oval:product_name>
<oval:product_version>3</oval:product_version>
<oval:schema_version>5.10</oval:schema_version>
<oval:timestamp>2023-04-28T06:17:58</oval:timestamp>
<oval:content_version>1682662678</oval:content_version>
</generator>
<definitions>
<definition class="vulnerability" id="oval:com.redhat.cve:def:20042779" version="636">
<metadata>
<title>CVE-2004-2779 libid3tag: id3_utf16_deserialize() misparses ID3v2 tags with an odd number of bytes resulting in an endless loop (low)</title>
<reference ref_id="CVE-2004-2779" ref_url="https://access.redhat.com/security/cve/CVE-2004-2779" source="CVE"/>
<description>DOCUMENTATION: The MITRE CVE dictionary describes this issue as: id3_utf16_deserialize() in utf16.c in libid3tag through 0.15.1b misparses ID3v2 tags encoded in UTF-16 with an odd number of bytes, triggering an endless loop allocating memory until an OOM condition is reached, leading to denial-of-service (DoS).</description>
<advisory from="secalert@redhat.com">
<severity>Low</severity>
<updated date="2021-10-21"/>
<cve cvss3="3.3/CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:L" cwe="CWE-400" href="https://access.redhat.com/security/cve/CVE-2004-2779" impact="low" public="20041231">CVE-2004-2779</cve>
<affected>
<resolution state="Affected">
<component>libid3tag</component>
<component>libid3tag-devel</component>
</resolution>
</affected>
<affected_cpe_list>
<cpe>cpe:/a:redhat:rhel_extras:7</cpe>
<cpe>cpe:/a:redhat:rhel_extras_oracle_java:7</cpe>
<cpe>cpe:/a:redhat:rhel_extras_rt:7</cpe>
<cpe>cpe:/a:redhat:rhel_extras_sap:7</cpe>
<cpe>cpe:/a:redhat:rhel_extras_sap_hana:7</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7::client</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7::computenode</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7::container</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7::containers</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7::server</cpe>
<cpe>cpe:/o:redhat:enterprise_linux:7::workstation</cpe>
</affected_cpe_list>
</advisory>
</metadata>
<criteria operator="OR">
<criterion comment="Red Hat Enterprise Linux must be installed" test_ref="oval:com.redhat.cve:tst:20042779006"/>
<criteria operator="AND">
<criterion comment="Red Hat Enterprise Linux 7 is installed" test_ref="oval:com.redhat.cve:tst:20042779005"/>
<criteria operator="OR">
<criteria operator="AND">
<criterion comment="libid3tag-devel is installed" test_ref="oval:com.redhat.cve:tst:20042779001"/>
<criterion comment="libid3tag-devel is signed with Red Hat redhatrelease2 key" test_ref="oval:com.redhat.cve:tst:20042779002"/>
</criteria>
<criteria operator="AND">
<criterion comment="libid3tag is installed" test_ref="oval:com.redhat.cve:tst:20042779003"/>
<criterion comment="libid3tag is signed with Red Hat redhatrelease2 key" test_ref="oval:com.redhat.cve:tst:20042779004"/>
</criteria>
</criteria>
</criteria>
</criteria>
</definition>
.....
</definitions>
<tests>
<red-def:rpmverifyfile_test check="at least one" comment="Red Hat Enterprise Linux 7 is installed" id="oval:com.redhat.cve:tst:20042779005" version="636">
<red-def:object object_ref="oval:com.redhat.cve:obj:20042779003"/>
<red-def:state state_ref="oval:com.redhat.cve:ste:20042779002"/>
</red-def:rpmverifyfile_test>
......
</tests>
<objects>
<red-def:rpmverifyfile_object id="oval:com.redhat.cve:obj:20042779003" version="636">
<red-def:behaviors noconfigfiles="true" noghostfiles="true" nogroup="true" nolinkto="true" nomd5="true" nomode="true" nomtime="true" nordev="true" nosize="true" nouser="true"/>
<red-def:name operation="pattern match"/>
<red-def:epoch operation="pattern match"/>
<red-def:version operation="pattern match"/>
<red-def:release operation="pattern match"/>
<red-def:arch operation="pattern match"/>
red-def:filepath/etc/redhat-release</red-def:filepath>
</red-def:rpmverifyfile_object>
......
</objects>
<states>
<red-def:rpmverifyfile_state id="oval:com.redhat.cve:ste:20042779002" version="636">
<red-def:name operation="pattern match">^redhat-release</red-def:name>
<red-def:version operation="pattern match">^7[^\d]</red-def:version>
</red-def:rpmverifyfile_state>
......
</states>
</oval_definitions>上文首先从generator得到是RedHat在2023-04-28T06:17:58发布的基于ova l5.4版本协议格式的内容,其次摘取了一个完整元素描述,oval:com.redhat.cve:def:20042779定义的漏洞CVE-2004-2779,在(1)oval:com.redhat.cve:tst:20042779005 安装了Red Hat Enterprise Linux 7 , (2) oval:com.redhat.cve:tst:20042779001 安装了libid3tag-devel且 oval:com.redhat.cve:tst:20042779002 软件使用Red Hat redhatrelease2 key签名 , (3) oval:com.redhat.cve:tst:20042779003 安装了libid3tag 且 oval:com.redhat.cve:tst:20042779004 软件使用Red Hat redhatrelease2 key签名 ,满足(1)(2)或(1)(3)即可判断出存在漏洞CVE-2004-2779。
参考文献
[1] https://github.com/g0dA/linuxStack/blob/master/OVAL/OVAL%E5%AD%A6%E4%B9%A0.md
[2] https://zh.wikipedia.org/zh-sg/%E6%BC%8F%E6%B4%9E
[3] https://github.com/Sep0lkit/Blog/issues/9
[4] https://oval.mitre.org/